Treat Detection & Response
How quickly can you answer the most important question:
“Is our data safe?”
DBTRONIX drastically reduces the time to detect and respond to cyberattacks – spotting threats that traditional products miss. By combining visibility and context from both cloud and on-prem infrastructure, DBTRONIX customers get:

90% reduction in incident response times

Out-of-the-box threat models for the entire kill chain

“We don’t know if any
data was stolen.”
Many SOCs lack visibility into what users are doing with data, which devices they’re using, and where they connect from.
Without context, alerts are confusing and imprecise, and analysts spend far too much time grepping through logs to figure out who the user is, whether their behavior is normal, and whether the data they touched is important.
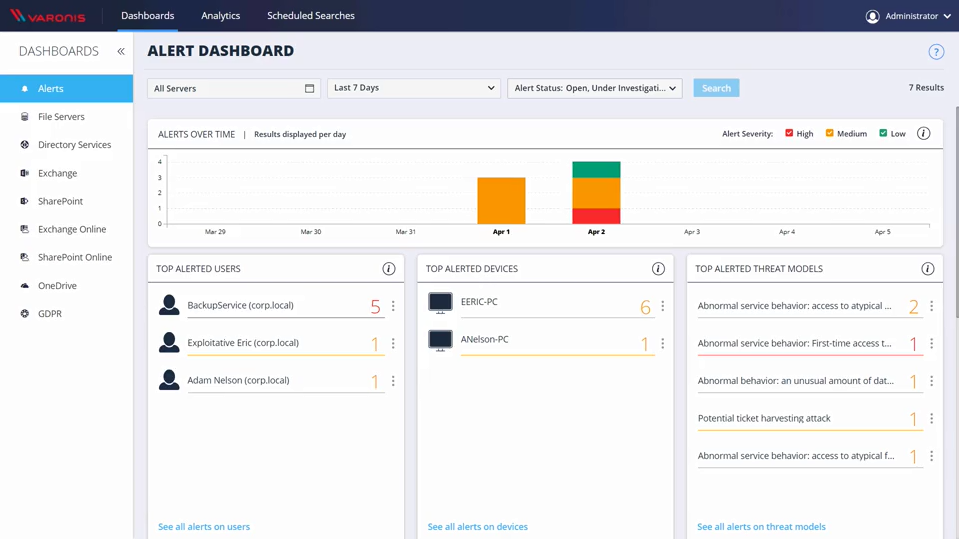
How quickly and accurately can DBTRONIX answer: “Is our data safe?”
Watch a short video demo!
Close the gap in your security stack with enriched, conclusive forensics
DBTRONIX has the essential ingredients to quickly detect, investigate, and respond to threats to your most important data and systems. The platform uses machine learning to build peace-time profiles over hours, days and weeks for every user and device, so when they behave abnormally, they get noticed.
Data
- Who has access to sensitive files and emails?
- Who is using data on-premises and in the cloud?
- Is any data access suspicious or abnormal?
Active Directory
- Who is using which device?
- Which accounts are logging into which computers?
- Have there been any abnormal changes to security groups or GPOs?
Edge Devices and DNS
- Who is connecting to our VPN? From where?
- Are any suspicious DNS requests being made?
- Are users uploading sensitive data to insecure websites?
See the full story of an attack from your core to the perimeter
DBTRONIX’ out-of-the-box threat models built by world-class researchers combine telemetry from multiple sources to detect threats other products are silent about. No need to write complex correlation rules and ad-hoc queries to make sense of seemingly unrelated events.
All
Data
Active Directory
Edge
Potential ticket harvesting attack.
BackupService logged into Jim-PC for the first time.
Abnormal access of GDPR data by a service account.
First time access to the internet by BackupService.
Data exfiltration via DNS tunneling.
The ultimate correlation engine
Auto-account discovery
Privileged users, service accounts, and executives are automatically identified based on their behavior.
Personal device pairing
Users are auto-paired with their personal devices making it easier to detect when an account has been compromised.
Working hours
A profile of each human user’s normal working hours helps flag suspicious after-hours activity.
IP resolution
DBTRONIX automatically resolves IP addresses to hostnames and geolocations, giving analysts helpful context and saving time.
Peer analysis
Each user is benchmarked against their peers and DBTRONIX alerts you when they deviate from normal activity for their role.
Threat intelligence
URL reputation enrichment separates risky connections from normal ones.
Resolve security incidents quickly and conclusively
Make junior analysts look like battle-tested blue teamers with intuitive forensics and incident response tools.
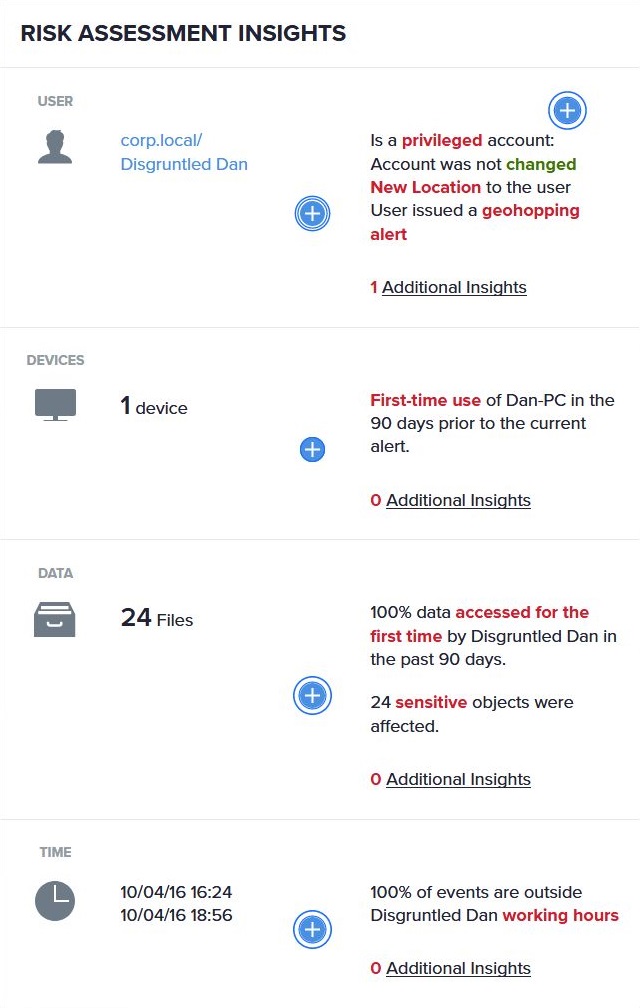
Context-rich insights
Is this alerted user on a watch list? Have they triggered any other alerts recently? Do they normally access sensitive data?
Analysts can quickly determine whether an alert represents a real threat or an insignificant anomaly–without spending hours stitching together logs.
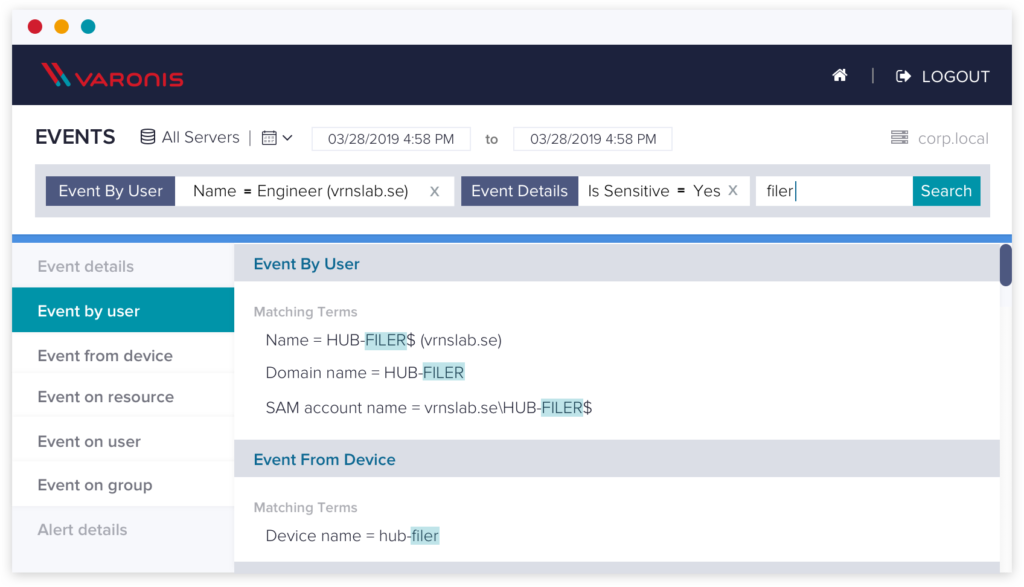
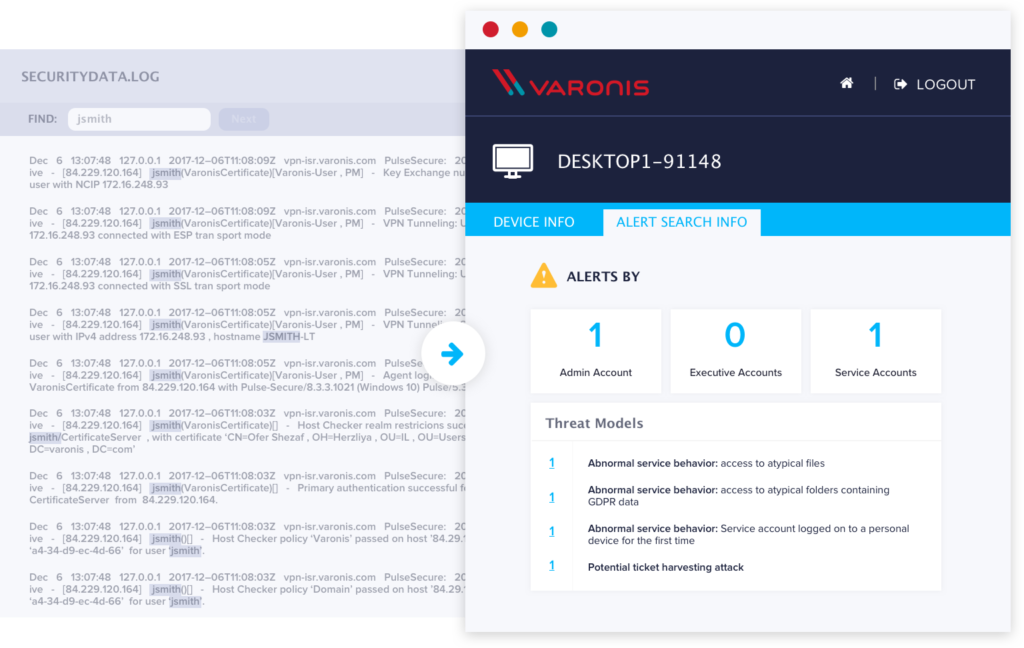
Lightning fast search
Want to see what a compromised user did? How about their laptop?
A single search immediately surfaces all activity for a user or device. No need to perform multiple ad-hoc queries or run complex reports.
Incident response playbooks
Each alert has an expert-built checklist for responding to an incident, covering everything from communications to containment to recovery, along with actionable steps to eradicate threats and improve security postures for future attacks.
Detection and Analysis
See what’s been detected – get details on the threat model and why it was triggered. Discover additional analysis needed in order to investigate, and tips on the right questions to ask.
Incident Notification
Learn who you need to notify based on this type of alert or incident. This might range from the CIO to IR teams to regulatory bodies.
Containment, Eradication, and Recovery
Get a best practices checklist with concrete steps to contain the potential threat, reduce outstanding risk, and recover from any damage.
Improve Future Detection
Follow concrete steps to help improve future detection and avoid this from happening again.
Next Steps
Dive deeper into events, users, devices, and data. Manage the alert status and add notes directly in the UI.
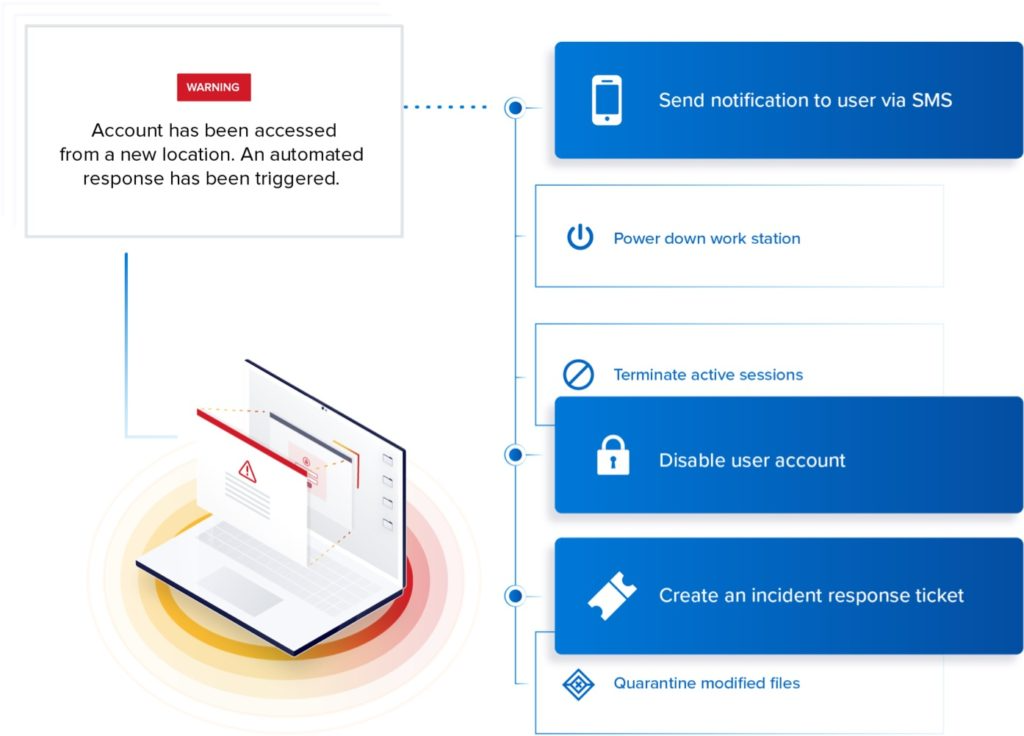
Automated response
Contain threats instantly by automatically triggering custom scripts to power down a machine, kill a connection, lock an account, and more. The power is in your hands.

See the full story of an attack from your core to the perimeter
DBTRONIX is Gartner’s most-reviewed platform for File Analysis and User and Entity Behavior Analytics, with more five-star reviews than any other vendor.
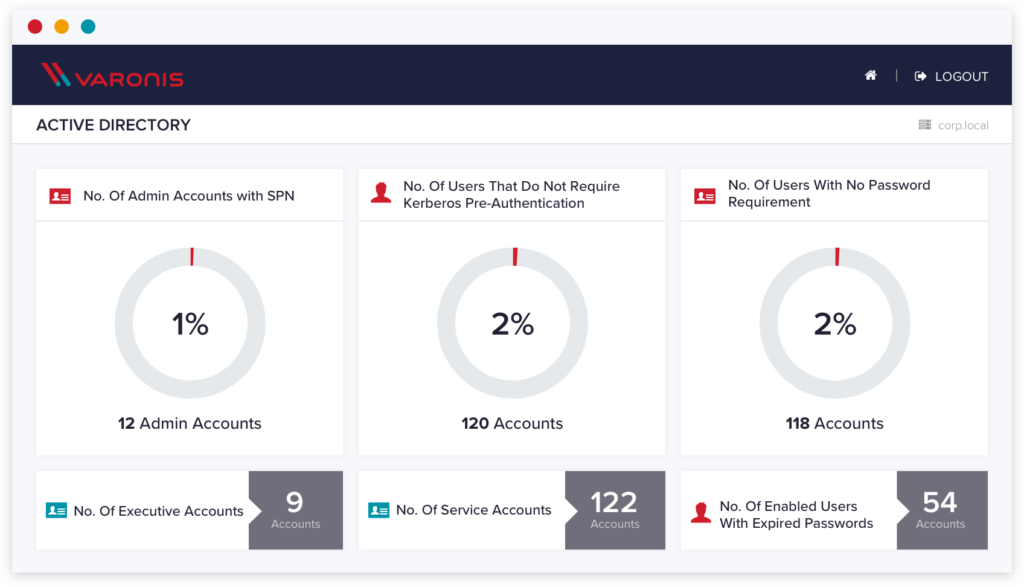
Find Active Directory
vulnerabilities before attackers do
Our Active Directory risk dashboard highlights dozens of legacy settings and misconfigurations that hackers can leverage for privilege escalation, lateral movement, and domain-wide compromise.
Integrate with the apps you love.






Contact Us
We are here to help. Call us and speak with a secure erase specialist who will answer any questions you might have




