DatAdvantage
Data-Centric Audit and Protection
DatAdvantage is the heart of our Data Security Platform, giving you complete visibility and control over your critical data and hybrid IT infrastructure.

We bring data security
and cost-savings together
DatAdvantage maps who can access data and who does access data – across file and email systems, shows where users have too much access, and then safely automates changes to access control lists and security groups.
Visualize who can access sensitive and regulated information
Audit every single file and email touch on-premises and in the cloud
Simulate changes in a sandbox and safely commit them when ready
Eliminate repetitive clean-up projects and automate manual data protection tasks
Assess, prioritize, and mitigate your biggest IT security risks
Our dashboards show where you’re at risk, and track your progress as you lock things down. Quickly pinpoint exposed folders, stale data, or inactive accounts that are still enabled. With Data Classification Engine, which looks inside files, you’ll also see where you have regulated and sensitive data that’s at risk.
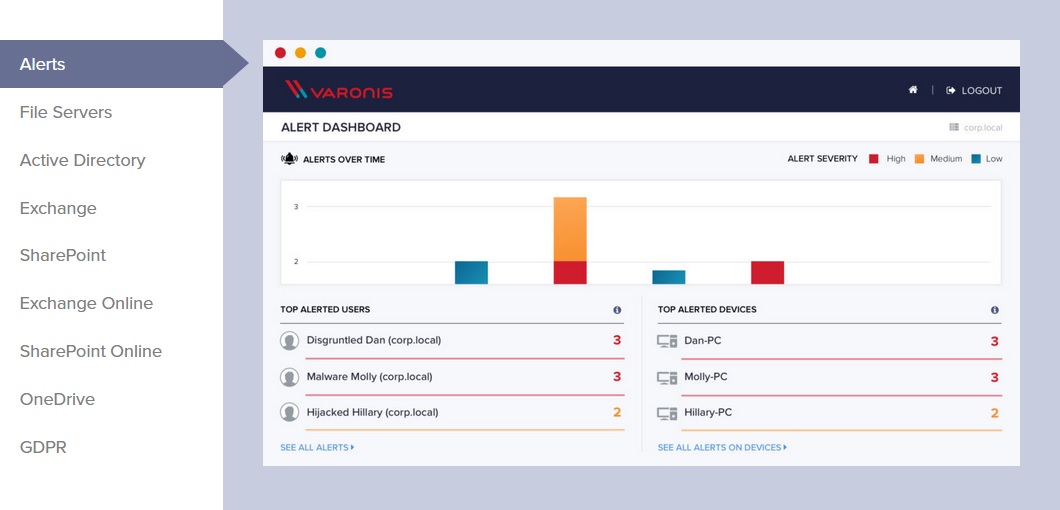
Get a panoramic view of data access
DatAdvantage has a bi-directional view: just double-click on a folder, site, or mailbox to see who has access to it, or click on a user or group to see everything they can access – across all your data stores. DatAdvantage figures out nested groups, permissions, inheritance, and even identifies folders where permissions aren’t functioning correctly.
Simulate and commit changes to safely remediate risk
A powerful commit engine can simulate access control changes in a sandbox and commit them when ready. DatAdvantage tracks and reports on multiple jobs, prevents errors with logic checks, and rolls changes back if needed.
Take remediation a step further. Automation Engine finds and safely fixes global groups and inconsistent permissions on entire servers with just a few clicks, making remediation projects exponentially faster than manual techniques.

Search a Unified Audit Trail of Events
With a unified audit trail, admins or security analysts are only a few clicks away from knowing who’s been opening, creating, deleting, or modifying important files, sites, Azure Active Directory objects, emails, and more.
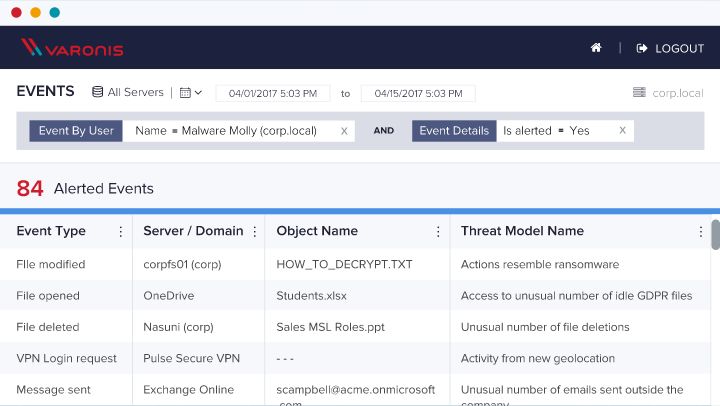
Investigate security incidents and troubleshoot issues with a searchable, sortable interface. See a user’s activity across cloud and on-premises systems in a single view. Your complete audit history is always at your fingertips – there’s no need to roll or archive logs.
AI-Powered
Recommendations
Our machine learning algorithm flags users with unnecessary access. Acting on these recommendations is a fast and accurate way to reduce risk and get to least privilege. Model permissions changes in a sandbox and commit changes to Office 365 with just a few clicks.

Schedule a personalized
data risk assessment
Our assessments are 100% obligation-free and non-intrusive
A dedicated engineer will do all the heavy-lifting and you’ll get a comprehensive report that highlights at-risk sensitive data, flags access control issues, and quantifies risk – so that when you’re asked what you’re doing to prevent becoming the next cybersecurity headline, you’re already ahead of the game.

Deep coverage of enterprise data stores
Unlike many products that take the mile-wide, inch-deep approach, DBTRONIX is consistently extending its full suite of data security functionality to the systems that are most important to our customers.

Active Directory
Windows
Sharepoint
Exchange
UNIX/Linux
Office 365

Dell EMC

NetApp

Nasuni

HPE

box
Perimeter Telemetry

DNS

Proxy

VPN
Deep coverage of enterprise data stores
Unlike many products that take the mile-wide, inch-deep approach, DBTRONIX is consistently extending its full suite of data security functionality to the systems that are most important to our customers.

Active Directory
Windows
Sharepoint
Exchange
UNIX/Linux
Office 365

Dell EMC

NetApp

Nasuni

HPE

box
Perimeter Telemetry

DNS

Proxy

VPN
Leverage dozens of built-in reports
Get trend reports, reports on permissions, active data, stale data, things that’ve changed, and things that need to be fixed. Run reports on demand, or schedule them for automatic delivery.
Uncover misconfigurations and security gaps
Dashboards and reports help you find and fix things like overexposed sensitive data, misconfigured Active Directory settings, broken permissions, and more.
Monitor privileged accounts
DatAdvantage auto-identifies executives, service accounts, and admins based on user behavior, group memberships, and other metadata. DBTRONIX builds a baseline of normal activity and alerts you when anything anomalous happens.
Find and archive stale data
DatAdvantage isolates stale data based on actual access activity from human users. Use Data Transport Engine’s flexible rules engine to automatically archive unused data based on your retention policies.
Detect internal and external threats with DatAlert
With DatAlert, get notified when something needs urgent attention – like someone accessing or encrypting a bunch of sensitive files, reading an executive’s email, or making changes to group policy outside of normal change control hours.
Identify and involve data owners
Identify owners through DatAdvantage, and then assign them, so they get reports about their data and their groups automatically. With DataPrivilege, you can give owners control – so they can safely manage and review access without IT’s help.
Frequently Asked
Questions
What hardware/software do I need?
Does DBTRONIX need to run as Domain Admin?
Is there any performance impact on my production servers?
Do you require agents to get audit events?
Ew, agents?
What's a free risk assessment?
Contact Us
We are here to help. Call us and speak with a secure erase specialist who will answer any questions you might have




