DatAlert
Data-Centric Threat Detection & Response
Say goodbye to dead-end investigations and mountains of raw logs. Confidently answer the question, “is my data safe” with user behavior analytics that just works.
Catch threats other security solutions miss
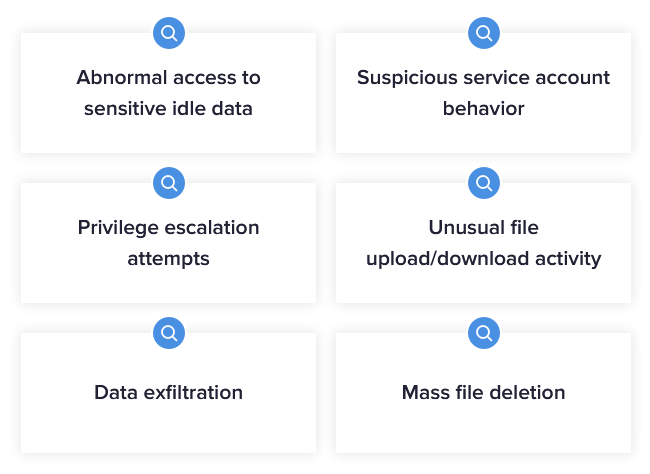
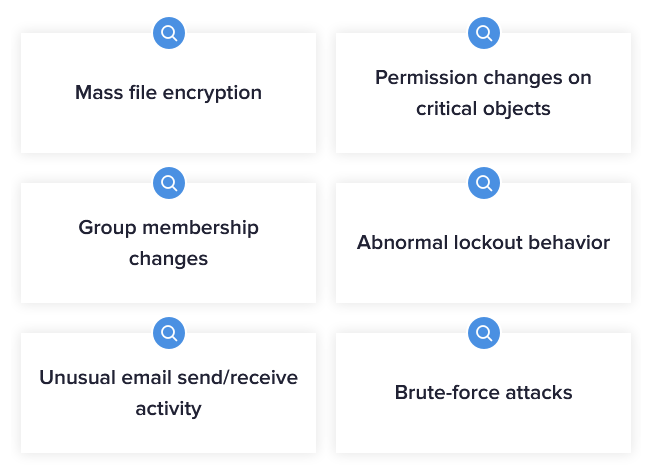
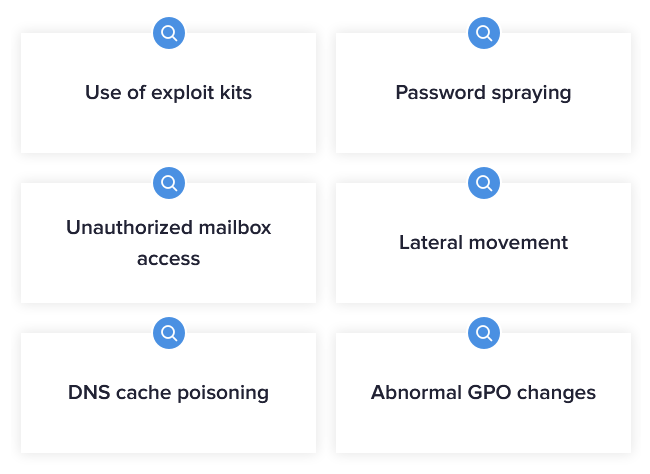
If you’re watching what’s happening with your data, attackers can’t hide. DBTRONIX combines a unique set of ingredients to uncover threats across the kill chain, like suspicious data access, abnormal logon attempts, and DNS exfiltration.
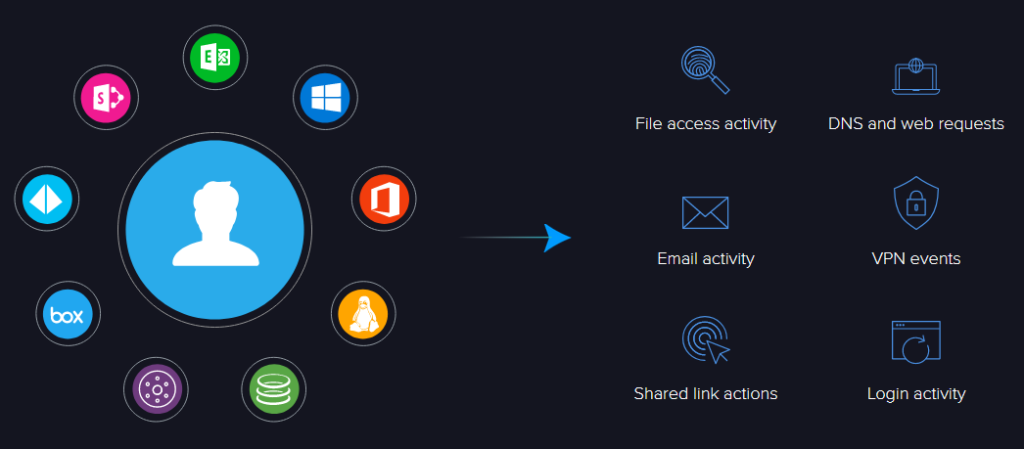
How it Works

“DatAlert noticed the anomalous behavior right away, which helped us get ahead of the infection proactively…
without DBTRONIX, we wouldn’t have known it was happening until it was much worse.”

Fewer alerts, more answers
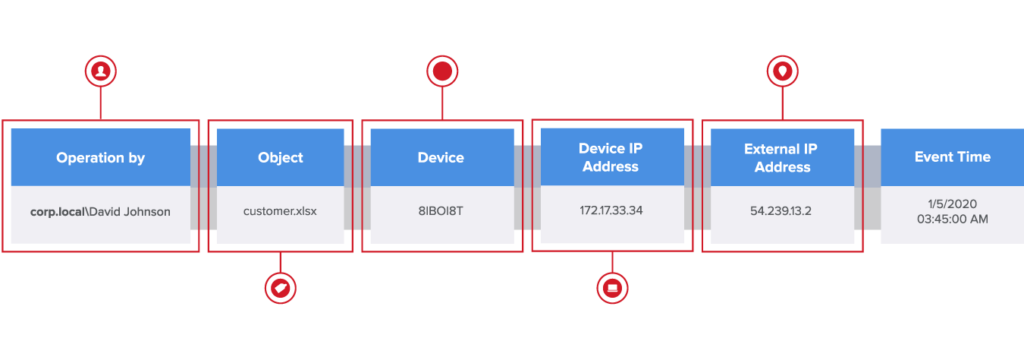
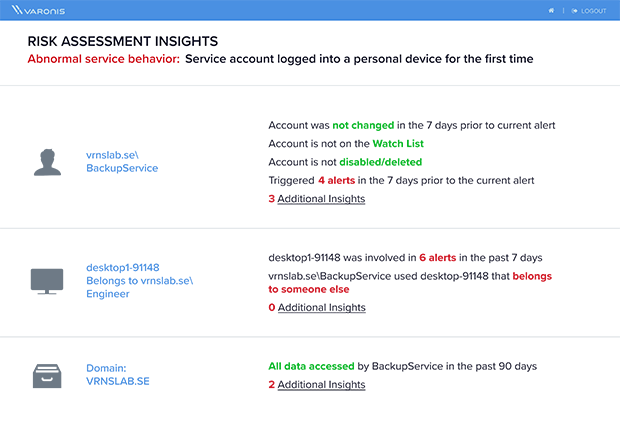
Quickly determine whether an alert represents a real threat or an insignificant anomaly without spending hours stitching together logs. Then, put alerts in a broader context: Is this alerted user on a watch list? Have they triggered any other alerts recently? Do they normally access sensitive data?

The most highly-rated UEBA solution on Gartner Peer Insights
Get expert Incident Response help—for free
Our Incident Response team can help you investigate all kinds of attacks—from ransomware, to APTs, to insider threats, and more. We offer this service for free to customers and prospects.
Meet some of our analysts
Matt Radolec
Director, Security Architecture & Incident Response
Ryan O’Boyle
Security Analytics Manager
Ian McIntyre
Security Analyst, Incident Response
Madeleine Massee
Security Analyst, Incident Response
See results next week, not next year
“DBTRONIX detected behavioral patterns of ransomware and immediately disabled the impacted user to stop this behavior in its tracks. DBTRONIX is the sole reason we were able to react so quickly, especially since the alert was detected outside of business hours.”
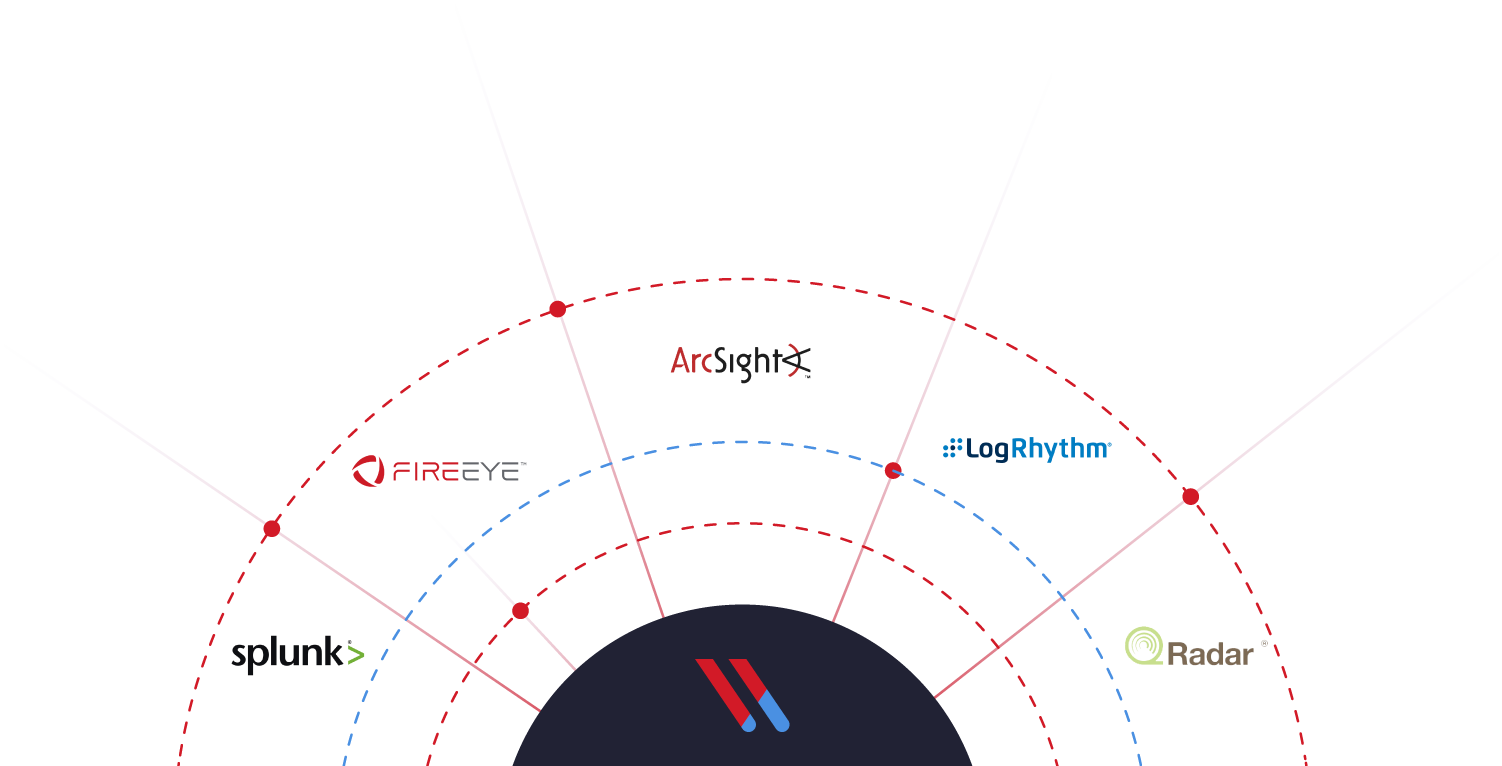
Bring data-centric visibility to your SIEM
without breaking the bank
Increase the power of your SIEM with data-centric insights from DBTRONIX. Send high-fidelity alerts (not raw logs) for correlation and investigation via syslog, SNMP, or one of our ready-made connectors.
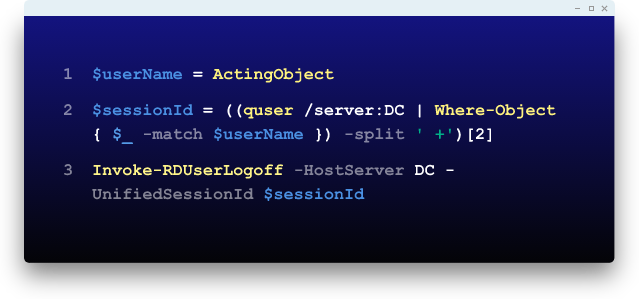
Don’t just detect, block.
Automated responses that can end users’ sessions, change passwords, etc. can stop attacks in their tracks and limit damage.
Powering 88% faster investigations
Auto-account discovery
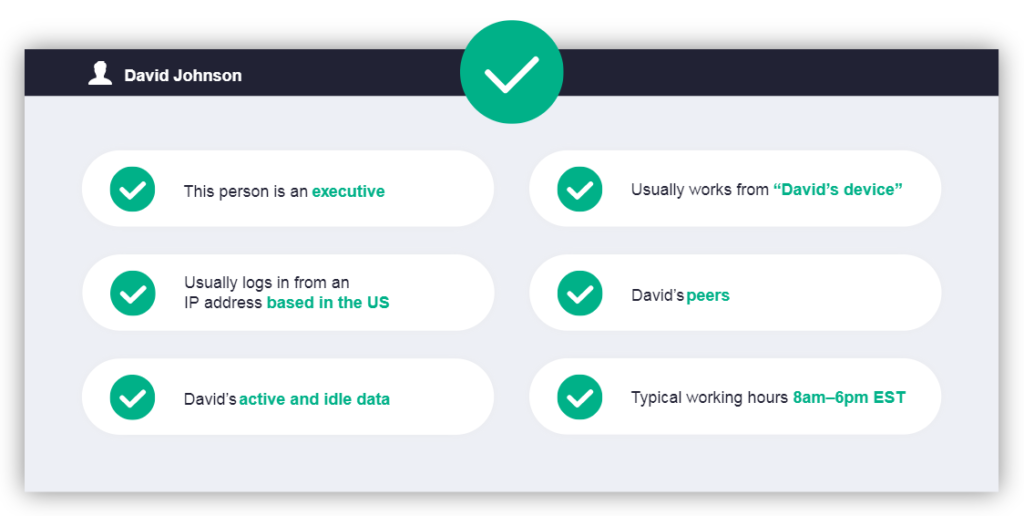
Privileged users, service accounts, and executives are automatically identified based on their behavior.
Behavior analysis
Our security experts and data scientists continually introduce new behavior-based threat models to monitor patterns, track the latest APTs, and keep your data safe.
Personal device pairing
Users are auto-paired with their personal devices making it easier to detect when an account has been compromised.
Working hours and geolocation
A profile of each human user’s normal working hours and geolocation helps flag suspicious after-hours or atypical activity.
IP resolution
DBTRONIX automatically resolves IP addresses to hostnames and geolocations, giving analysts helpful context and saving time.
Peer analysis
DBTRONIX benchmarks each user against their peers and alerts you when they deviate from normal activity for their role.
Threat intelligence
URL reputation enrichment separates risky connections from normal ones.
Incident response playbooks
Auto-updated built-in playbooks provide guided next steps for investigations and incident responses.
Gain access to our world-class cybersecurity services

Free Incident Response service
Call on DBTRONIX cybersecurity experts in the event of an incident
Free Purple Team exercise
Discover weak spots in your environment and bolster security defense

Free DatAlert optimization
Finetune DatAlert for your environment to enhance threat detection

Original, cutting-edge threat research
Learn about newly discovered strains of malware, APT activity, and ransomware
Frequently Asked
Questions
How much data can DBTRONIX monitor?
We have customers monitoring over 20PB of data while collecting and analyzing billions of events per day with DBTRONIX.
Our platform is built using a distributed event collection architecture, so it’s easy to scale up or down depending on your needs.
Will DatAlert slow down the systems that it’s monitoring?
No. DBTRONIX offloads the event collection from the servers we’re monitoring to a dedicated component called a collector. The resource impact on your servers will be trivial.
Does DatAlert require endpoint agents?
No. DBTRONIX monitors data stores, email, and Active Directory server-side, so there is no need to deploy endpoint agents.
Can I create my own alerts?
Yes. You can leverage out-of-the-box threat models as well as create custom alerts that are specifically designed for your data and your environment.
For example, you may choose to trigger an alert if an important folder’s permissions change or a specific user logs into a restricted system. The possibilities are endless.
Can I automate threat responses?
Does it integrate with other security products?
DBTRONIX integrates directly with LogRhythm, Splunk, ArcSight, ServiceNow, and QRadar, and supports more integrations via syslog.
Not sure if your integration is supported? Get in touch and we’ll work with you to find out.
How easy are threat models to deploy?
Is the learning period different for different threat models?
Want to see Edge in action?
Contact Us
We are here to help. Call us and speak with a secure erase specialist who will answer any questions you might have