EDGE
Stop Intrusion & Data Exfiltration
Edge combines data access with network activity to detect threats with a high signal-to-noise ratio. From APT intrusions to data exfiltration, Edge expands your field of vision.
Catch more threats, without more work
Edge completes the picture by analyzing perimeter activity from VPN, DNS, and web proxy in context with data, email, and Active Directory behavior. Our threat models continually learn and adapt to behaviors specific to your organization.
Expand your detection window
Attackers hope to evade detection by blending into your noisy network. But DBTRONIX knows your organization better than your adversary. Our machine learning understands what’s normal and alerts you to what isn’t—for every user and device—from the inside out.
Data
- Insider threats
- Ransomware
- APTs & malware
- Phishing
- Infected attachments
- Data exfiltration
Active Directory
- Recon
- Lateral movement
- Privilege escalation
Edge
- Brute force
- Command & control
- Data exfiltration

“In terms of solutions, DBTRONIX Edge was our MVP. Edge directed us to the computers with suspicious DNS requests, correlated them with specific users, and showed us the addresses we needed to block.”

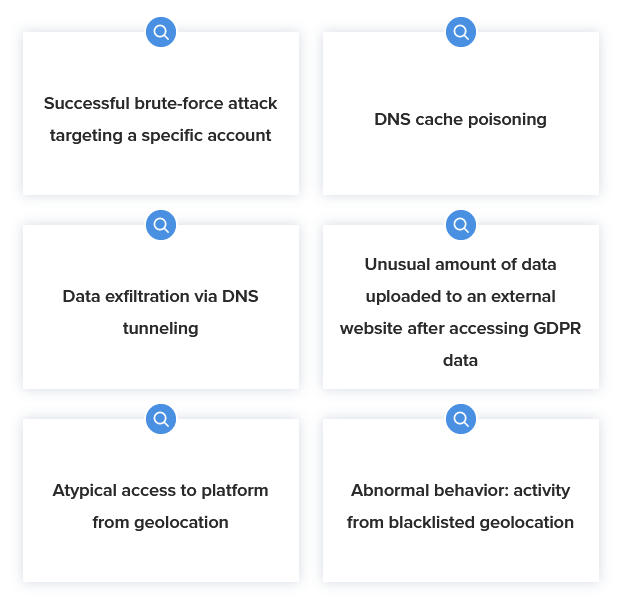
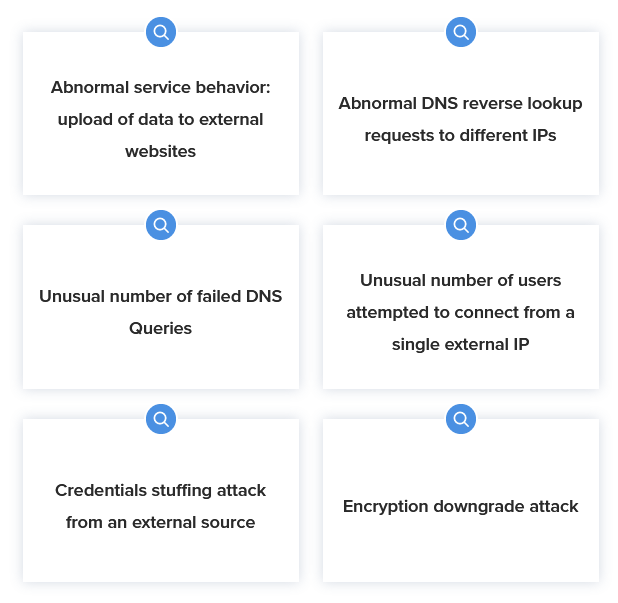
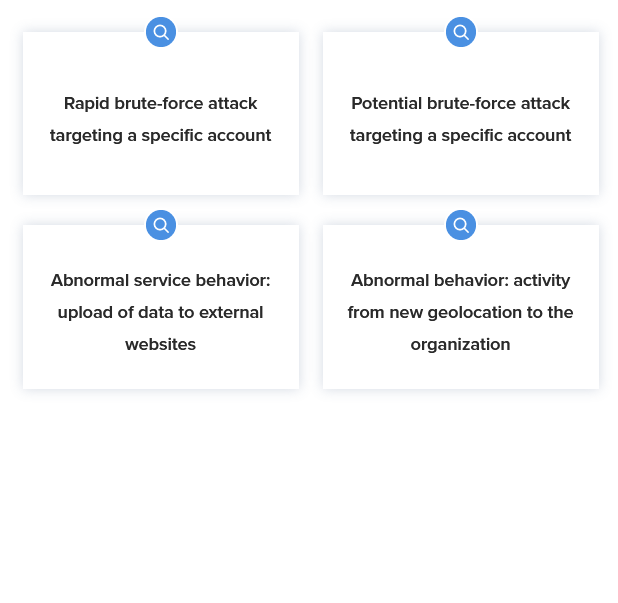
Threat hunt like a pro
Easily hunt for threats or flag policy violations like connections to known C2 domains or large uploads to web-based email sites. Automatically surface relevant events for further investigation. You can even build and save your own queries to jumpstart investigations.
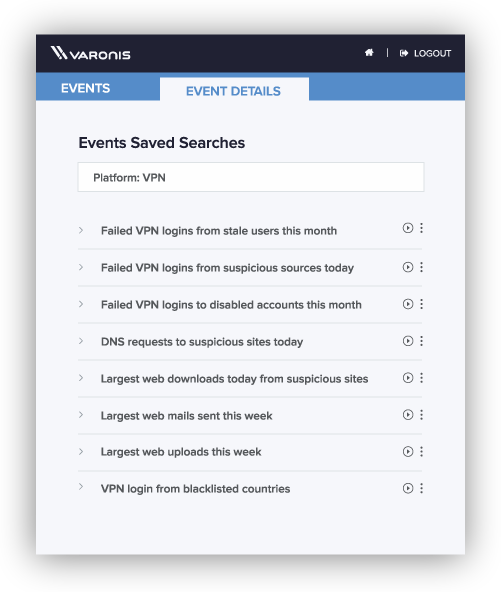
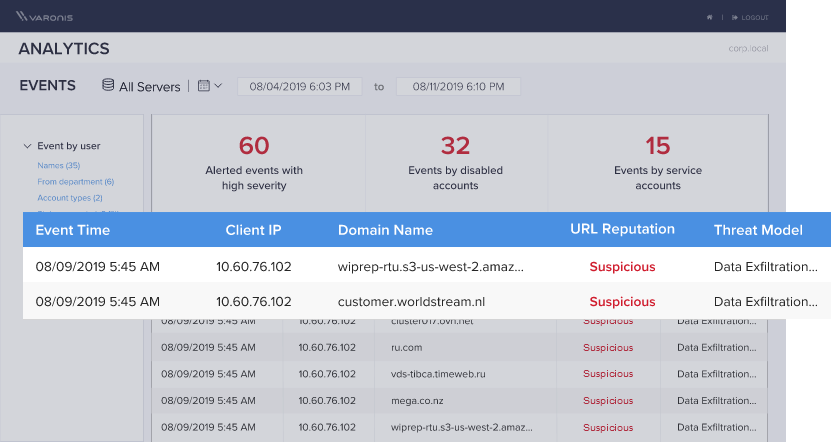
Event logs never looked this good
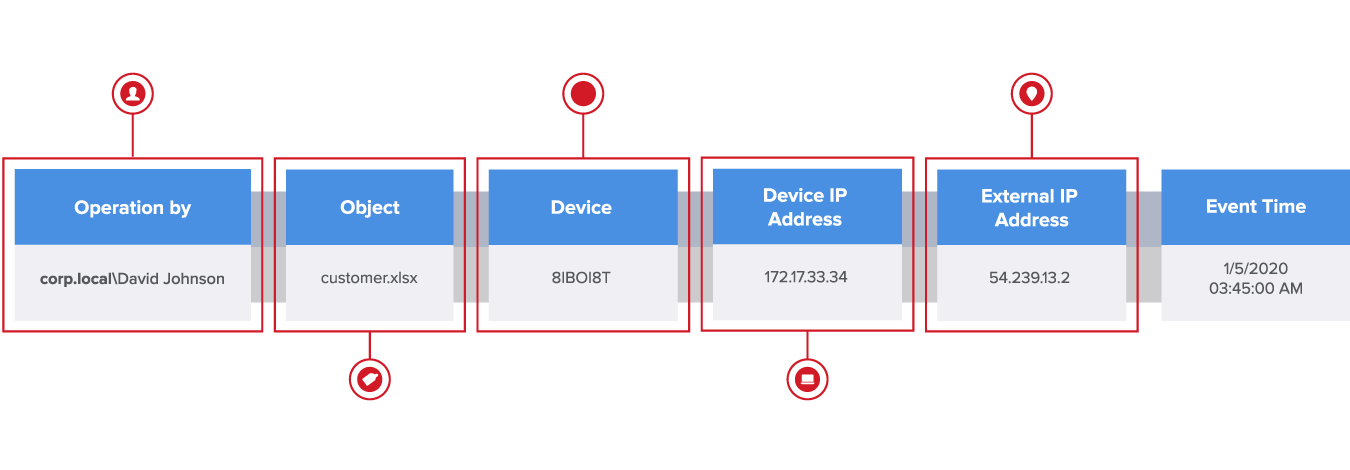
Logs from network devices are noisy, out-of-order, and each device type and vendor writes logs in their own way. DBTRONIX doesn’t just copy raw logs—we give you clean, human-readable events enriched with valuable context like URL reputation, account type, and data sensitivity.
Keep tabs on your personal data inventory
Keep a pulse on how much data you’ve indexed and any failed documents so that you always know the scope of your searches.
Avoid volume-based pricing
Ingest as much data as you need. Our fair pricing model protects you from big bills when network traffic surges.
Get fewer alerts, more answers
Turn billions of events into a handful of meaningful alerts with behavior-based detection, not clunky SIEM rules.
Investigate on your terms
Send alerts into your SIEM or investigate natively with our fast and powerful forensics tools.
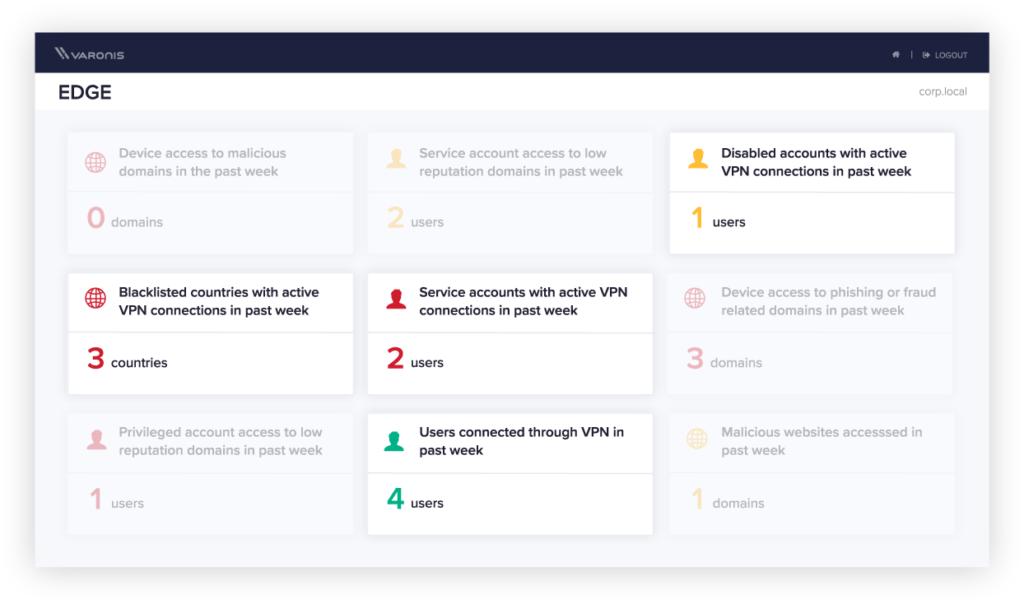
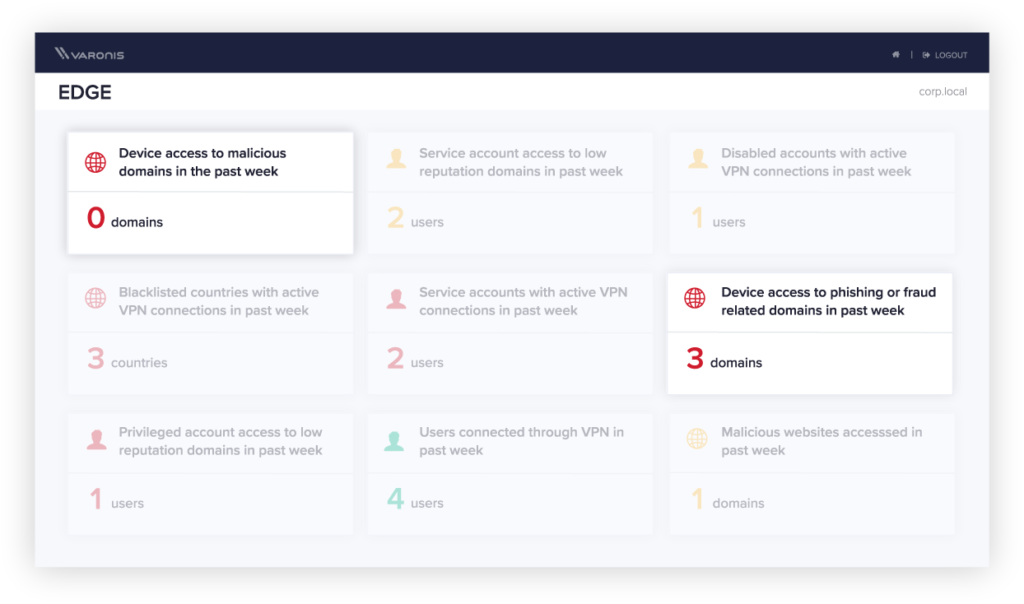
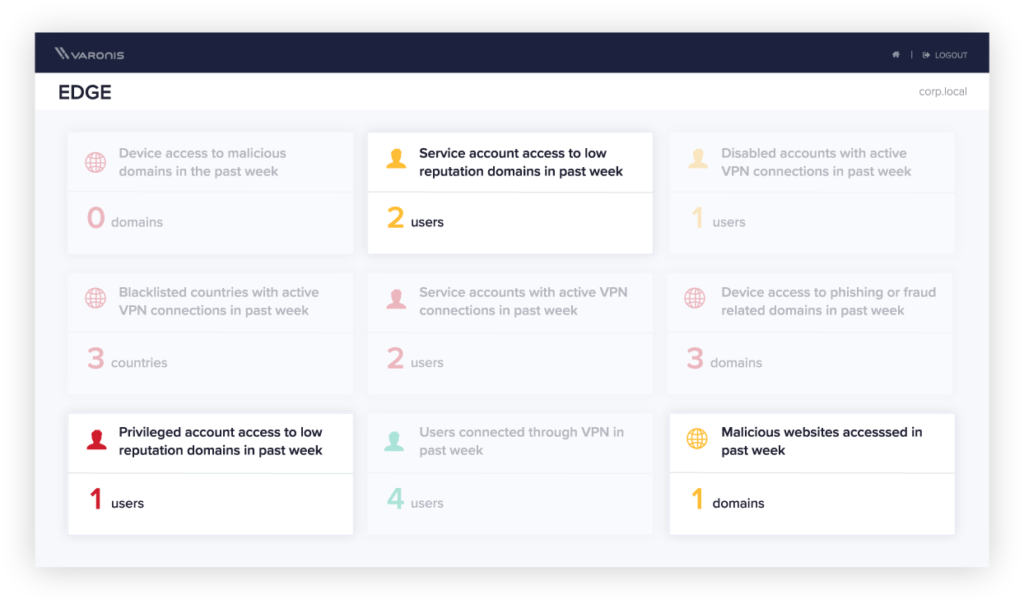
Real-time awareness of your top remote work risks
Visualize and report on indicators of compromise hiding in your network traffic.
Quick & conclusive investigations
When investigating an incident, it’s crucial to be able to quickly answer “Was any data stolen?” Pivot from suspicious perimeter activity to sensitive data access in seconds, without hopping between disparate tools and logs.

Filter suspicious events from any source

Isolate the top-offending user or device with one click

Easily answer “what data did they access?”
Resources from our world-class research team
Webinar

5 Ways Hackers are Exploiting Remote Workforces
Threat Research

DBTRONIX Exposes Global Cyber Campaign: C2 Server Actively Compromising Thousands of Victims
Read More
Free Trial

Start a free trial of DBTRONIX Edge
Contact Us
Frequently Asked
Questions
Which VPN vendors does Edge support?
CheckPoint, Cisco, F5, Fortinet, Palo Alto, Pulse Secure
Which web proxies does Edge support?
Apache, Cisco (IronPort), Forcepoint (WebSense), McAfee, Palo Alto, Squid, Symantec (Bluecoat), Zscaler
Which DNS does Edge support?
Microsoft DNS, Infoblox
How does Edge collect events?
Edge can collect events directly from the source devices using Syslog, or from Splunk or Filebeat. If the data is already collected in Splunk, you can configure DBTRONIX Edge to get the events directly from Splunk.
Which stages of the kill chain does Edge cover?
Does Edge require endpoint agents?
No. Edge monitors network devices, so there is no need to deploy endpoint agents.
Can I create my own alerts?
Can I automate threat responses?
Does DBTRONIX integrate with other security products?
Want to see Edge in action?
Contact Us
We are here to help. Call us and speak with a secure erase specialist who will answer any questions you might have